
Publisher:
Bonnie King
CONTACT:
Newsroom@Salem-news.com
Advertising:
Adsales@Salem-news.com

~Truth~
~Justice~
~Peace~
TJP
Jan-10-2013 12:49

 TweetFollow @OregonNews
TweetFollow @OregonNews
Hacker Hits on U.S. Power and Nuclear Targets Spiked in 2012
Michael Maloof Special to Salem-News.comConducting interviews on this topic is the former security policy analyst in the Office of the Secretary of Defense and the author of the newly released book "A Nation Forsaken", F. Michael Maloof.
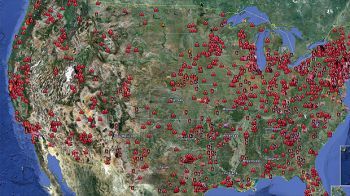 The Department of Homeland Security released this map showing the locations of 7,200 key industrial control systems that appear to be directly linked to the Internet and vulnerable to attack. Courtesy: U.S. Dept. of Homeland Security |
(CNN Money) - America's power, water, and nuclear systems are increasingly being targeted by cybercriminals seeking to gain access to some of the nation's most critical infrastructure.
The number of attacks reported to a U.S. Department of Homeland Security cybersecurity response team grew by 52% in 2012, according to a recent report from the team. There were 198 attacks brought to the agency's attention last year, several of which resulted in successful break-ins.
An earlier report from DHS sketched in details on some of those successes. An unidentified group of hackers targeting natural gas pipeline companies gained access to the corporate systems of several of their targets and "exfiltrated" -- that's security-speak for "stole" -- data on how their control systems work.
The information obtained "could facilitate remote unauthorized operations," DHS said. There's no evidence the hackers have actually broken into the control systems themselves, the agency added.
The energy sector was the most-targeted field, with 82 attacks, and the water industry reported 29 attacks last year. Chemical plants faced seven cyber attacks, and nuclear companies reported six.
Hackers hit the bulls-eye on "several" of their nuclear targets: "These organizations reported that their enterprise networks were compromised and in some cases, exfiltration of data occurred," the DHS team wrote. It said that it is not aware of any successful breaches of nuclear control networks.
Those are only the attacks that we know about, though. Many companies choose not to report incidents, and the majority of cyberattacks go undiscovered, according to industry researchers.
Of course, it's not the quantity of attacks that matters. It's the small handful that succeed.
DHS warned that the nation's infrastructure is worryingly vulnerable. Using a special search engine that finds Internet-connected devices, researchers from security advocacy group InfraCritical located more nearly 500,000 devices across the country that appeared to tap into key control systems. They brought their list to DHS, which began investigating -- and confirmed that 7,200 devices on it really do appear to be linked to critical control systems.
Many of those systems are directly reachable through the Internet and "have either weak, default, or nonexistent logon credential requirements," the agency warned.
It is working with government agencies and private partners to alert system operators and close down those vulnerabilities.
Related story: Nations prepare for cyber war
A similar test of European home automation systems revealed that many of these devices had been built without security in mind. One popular smart meter device, for instance, had a default password of "1234."
Anyone with malicious intent -- terrorists, rogue or enemy nations -- could locate those devices just as easily as the researchers did.
The Obama administration and many in Congress have been more vocal about how an enemy nation or a terrorist cell could target the country's critical infrastructure in a cyberattack. Legislation aimed at preventing such attacks stalled in Congress last year.
In its report, the Department of Homeland Security advised critical infrastructure companies to keep devices linked to their control systems offline, put stronger passwords in place and implement better security protocols.
Some security experts think the nation won't crack down on securing its critical systems until there's a high-profile debacle.
"I believe that people will not truly get this until they see the physical implications of a cyber attack," Shawn Henry, who retired last year as the Federal Bureau of Investigation's top cybercrime official, said at an industry conference in July. "We knew about Osama bin Laden in the early '90s. After 9/11, it was a worldwide name. I believe that type of thing can and will happen in the cyber environment." To top of page
http://money.cnn.com/2013/01/
F. Michael Maloof, a former senior security policy analyst in the Office of the Secretary of Defense, has almost 30 years of federal service in the U.S. Defense Department and as a specialized trainer for border guards and Special Forces in select countries of the Caucasus and Central Asia. While with the Department of Defense, Maloof was director of technology security operations as head of a 10-person team involved in halting the diversion of militarily critical technologies to countries of national security and proliferation concern and those involved in sponsoring terrorism. His office was the liaison to the intelligence and enforcement community within the Office of the Secretary of Defense in halting transfers and using cases that developed from them as early warnings to decision-makers of potential policy issues.
Following the September 11, 2001, terrorist attack on the United States, Maloof was detailed back to report directly to the undersecretary of defense for policy to prepare analysis of worldwide terrorist networks, determine their linkages worldwide and their relationship to state sponsors.
Author Profile and Information, Click Here: http://wndbooks.wnd.com/a-
 |
 |
 |
Articles for January 9, 2013 | Articles for January 10, 2013 | Articles for January 11, 2013
Salem-News.com:

Quick Links
DINING
Willamette UniversityGoudy Commons Cafe
Dine on the Queen
Willamette Queen Sternwheeler
MUST SEE SALEM
Oregon Capitol ToursCapitol History Gateway
Willamette River Ride
Willamette Queen Sternwheeler
Historic Home Tours:
Deepwood Museum
The Bush House
Gaiety Hollow Garden
AUCTIONS - APPRAISALS
Auction Masters & AppraisalsCONSTRUCTION SERVICES
Roofing and ContractingSheridan, Ore.
ONLINE SHOPPING
Special Occasion DressesAdvertise with Salem-News
Contact:AdSales@Salem-News.com



Terms of Service | Privacy Policy
All comments and messages are approved by people and self promotional links or unacceptable comments are denied.
[Return to Top]
©2026 Salem-News.com. All opinions expressed in this article are those of the author and do not necessarily reflect those of Salem-News.com.