
Publisher:
Bonnie King
CONTACT:
Newsroom@Salem-news.com
Advertising:
Adsales@Salem-news.com

~Truth~
~Justice~
~Peace~
TJP
Feb-20-2014 23:58


 TweetFollow @OregonNews
TweetFollow @OregonNews
Cry Cyber Terrorism is the New Cry Wolf
Dexter Phoenix Salem-News.comHacking has proven to be a reliable way of digging out the truth.
 |
(LONDON) - Times are changing in this so called land of the free, driven by political correctness that is strictly governed by think tanks from government and congress groups, that decide what is right or wrong on our behalf. Free thoughts, free speech and free behavior are now scrutinized emphatically by nanny state controlled agencies who thrive on changing the world around them.... to please their rather obscured concept on how life should be, when molded to their own version of what they think a civilized western culture should be.
There is still a breathing space when it comes to free speech, and expressing your own thoughts in public, or expressing it via writing. Even large groups of supporters or gatherings of protesters are still legal (in most countries)... but when it comes to expressing yourself via computer intervention “hacking” then it becomes illegal, under a set of laws that were set out by the Bush administration back in 2001.
The reason hackers are taking on such large and brazen attacks these days, is because all other methods of speaking out have fallen on deaf ears. People can only be ignored for so long, until desperate measures have to be taken.
Hacking has proven to be a reliable way of digging out the truth; thus justifying their complaints towards any subject that was sensitive enough to be hidden from the public eye. This of course has caused major headaches for the companies and agencies that they have been attacked, leaving no defence against the can of worms opened up by the hackers.

The terrorist act is now being used to full effect on everything that is deemed to be detrimental to their beliefs, interests or policies. It has now reached the point where, if views are expressed which are considered to be inflammatory, you run the risk of being flagged as a threat to national security, putting you straight under the banner of the anti-terrorist act.
At the very least someone, somewhere, will have opened a new file with your name on it! Sadly this anti terrorist law is being overused and abused, to make the authorities' lives easier when it comes to arresting or subduing anyone that might annoy them.
The anti terrorist laws take away all your rights (perfect if the assailant was a hardcore terrorist hell bent on killing peoples lives) but not so good when it is used on normal everyday person. This is like taking a sledgehammer to crack an egg; excessive, and counter-productive. This draconian behavior has actually backfired in the past few years, turning people against their own system (hacker groups, hacker attacks, and people generally learning to be hackers and script kids have come on the increase ten fold since 2001).

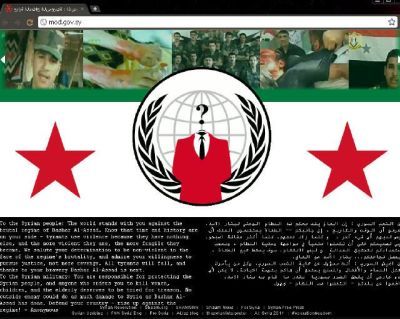

Recently, four professional hacker groups have been in the cross-hair with western authorities. Syrian (Syrian Electronic Army), Iran, China (China’s People’s Liberation Army)... not including a million other tech savvy people that are hacking from China), and the infamous Anonymous (worldwide). They are not regulated or controlled so much these days, and a few Anonymous ring leaders have been caught and arrested, and coerced into working for their arch nemesis, as an alternative to spending time in prison.
Anonymous used to have original ringleaders that semi-regulated their causes through people of the LulzSec group. Controlled by Topiary who finally got caught by the Feds, which brought on a widespread "Free Topiary" movement. Dmitriy Guzner, an American nineteen- year old, was also caught under the "unauthorized impairment of a protected computer act" in November 2009. He was sentenced to 366 days in a US Federal prison. Chris Doyon (known as Commander X), a self confessed leader of Anonymous, was arrested in September 2011. He “apparently” jumped bail in February 2012, and did the proverbial run across the border into Canada. A bit too close to home to say the least. His skills could easily been brought out by various companies, with huge law firm backings to protect his valuable experience overseas.
In September 2012, journalist Barret Brown - known for speaking to media on behalf of the Anonymous group - was also arrested. Allegedly Barret had a wealth of information when it came to the backbone of the Anonymous syndicate, which would have been useful to the FBI. Unlike many other groups or companies, Anonymous has the same ability as that infamous Greek mythology beast ...the “Lernaean Hydra”. You chop off one of its heads, another one will grow back.

Anonymous are now a free-for-all hackers group that are creating faction groups all over the world - attacking companies and agencies whose ethics are deemed to be questionable. They have attacked the FBI, CIA, MI6, MI5, as well as other large corporations, but they have not been put under the red flag label of terrorism.
However, the hacker groups of China, Iran and Syria have been given that label... even Israel has been hacking into sensitive information on the CIA servers (does that make them terrorists as well?).

To make things worse, these groups who are obviously just as patriotic as the Americans when it comes to protecting their own beliefs, countries and cultures, that are now being accused of being part of a more malicious consortium... are all part of or working for the governments and presidents of their own countries. This puts them under the hardest Terrorism act out there.
This of course is absurd.
This is like saying that a hacker that supports the Obama administration works for Obama directly. Even though Anonymous shares its manifesto with a worldwide audience, and does some pretty impressive damage, they have never been accused of being terrorist groups.
The Syrian, Iranian and Chinese hackers groups, who have utilised exactly the same tactics, have unfairly come under such stereo typed labeling. These particular people are frequently only sharing their frustration with the biased one-sided news reports that seem to be hell bent on ruining their own country. This is like accusing Obama of being an evil tyrant. Consequentially the rest of America must be tarred with the same brush.

Until we get fair, non-biased, news on both sides of the fence, not being manipulated by political groups or agencies for their own personal vendetta or interests, you will always get people to stand up for their own country, rights, and beliefs ...and why not?
What they are doing is no different than any other country. It doesn’t make them terrorists or Jingoists. Their acts are not belligerent in nature.
Unlike the old expression... one shoe does not fit all, and the same goes for countries that force their own beliefs on other countries and cultures, that are very different from their own.
Until countries learn to step back and respect other cultures and ideologies, hacking will always be on the increase. It seems to be the only reliable way forward to express the anger and frustration felt towards the hierarchy. Attacking such countries could lead to escalation as other nations take sides for and against. Intimidation and finger-pointing leads to the snowball effect - and that ever increasing boulder of snow as it charges down that mountain, has to land somewhere.
- Robert S. Mueller, III Director Federal Bureau of Investigation mentioned this on the F.B.I webpage.
http://www.fbi.gov/news/
Cyber
- As this committee knows, the cyber arena has significantly changed over the last decade. Cyber attacks and crimes are becoming more commonplace, more sophisticated, and more dangerous. The scope and targets of these attacks and crimes encompass the full range and scope of the FBI’s criminal investigative and national security missions.
- Traditional crime, from mortgage and health care fraud to child exploitation, has migrated online. Terrorists use the Internet to recruit, to communicate, to raise funds, to train and propagandize, and as a virtual town square, all in one. On a daily basis, we confront hacktivists, organized criminal syndicates, hostile foreign nations that seek our state secrets and our trade secrets, and for-profit actors willing to hack for the right price.

- Since 2002, the FBI has seen an 84 percent increase in the number of computer intrusions investigations. Hackers—whether state sponsored, criminal enterprises, or individuals—constantly test and probe networks, computer software, and computers to identify and exploit vulnerabilities. We are working with our partners, both foreign and domestic, to develop innovative ways to identify and confront the threat as well as mitigate the damage. There is always more work to be done, but we have had some success, including the 2011 takedown of Rove Digital, a company founded by a ring of Estonian and Russian hackers to commit a massive Internet fraud scheme.
- The Rove Digital scheme infected more than four million computers located in more than 100 countries with malware. The malware secretly altered the settings on infected computers, enabling the hackers to digitally hijack Internet searches using rogue servers for Domain Name System (DNS) routers and re- routing computers to certain websites and ads. The company received fees each time these websites or ads were clicked on or viewed by users and generated $14 million in illegitimate income for the operators of Rove Digital.
- We were able to work with our law enforcement counterparts in Estonia and our private industry partners to take down this criminal organization. Following the arrest of several co-conspirators in Estonia, teams of FBI agents, linguists, and forensic examiners assisted Estonian authorities in retrieving and analyzing data that linked the co-conspirators to the Internet fraud scheme. At the same time, we obtained a court order in the United States to replace the rogue DNS servers with court-ordered clean servers.

- In this case, we not only took down the criminal organization, but we also worked with our partners in the Department of Homeland Security (DHS) and other agencies to mitigate the damage. Seven individuals have been indicted in the Southern District of New York in this case: six in Estonia and one in Russia. The United States has sought extradition of all six Estonian subjects. To date, two of them have been remanded to U.S. custody, and both have pleaded guilty.
- We have also worked against infrastructure we believe has been used in distributed denial of service (DDoS) attacks, preventing it from being used for future attacks. Since October, the FBI and DHS have released nearly 168,000 Internet Protocol (IP) addresses determined to be infected with DDoS malware. We have released this information through joint indicator bulletins (JIBs) to 129 countries. Both the DHS’ Computer Emergency Readiness Team and FBI’s legal attachés released JIBs to our foreign partners. These actions have enabled our foreign partners to take action and reduced the effectiveness of the botnets and the DDoS attacks.
- Just as the FBI has transformed its counterterrorism and intelligence programs to deal with an evolving and adapting threat, the Bureau is strengthening its cyber program and capabilities.
- Computer intrusions and network attacks are the greatest cyber threat to our national security. To better prioritize our cyber resources on the greatest cyber threats, last year we focused our Cyber Division on computer intrusions and moved all other cyber- facilitated crimes that are perpetrated over the Internet to our Criminal Investigative Division.
- The FBI has also focused on hiring specialized personnel to address this growing threat. The FBI now has more than 1,000 specially trained agents, analysts, and digital forensic examiners that run complex undercover operations and examine digital evidence. The FBI is also the executive agent of the National Cyber Investigative Joint Task Force, which includes representatives from 19 law enforcement and intelligence agency partners. The task force operates through Threat Focus Cells— smaller groups of agents, officers, and analysts focused on particular threats.

- Both the Cyber Division and the NCIJTF are increasingly engaging the private sector in our effort to combat cyber threats.
- We distribute cyber threat information to victim companies, sometimes permitting them to stop cyber attacks before they happen. Appropriate two-way dialogue with the private sector is essential for the FBI to engage in time-sensitive investigative and disruption activities, including determining whether the cyber threat poses a threat to national security.
- U.S. law enforcement and intelligence communities, along with our international and private sector partners, are making progress.
- Technological advancements and the Internet’s expansion continue to provide malicious cyber actors the opportunity to harm U.S. national security and the economy. Given the consequences of such attacks, the FBI must be able to keep pace with this rapidly developing and diverse threat. Because of this, the FY 2014 budget request includes an additional 152 positions (60 special agents, one intelligence analyst, and 91 professional staff) and $86.6 million to help address this threat.
- The Justice Department submitted the ATA to Congress late last week as a response to the September 11th terrorist attacks in New York, Washington and Pennsylvania.

- As a "Federal terrorism offense," the five year statute of limitations for hacking would be abolished retroactively -- allowing computer crimes committed decades ago to be prosecuted today -- and the maximum prison term for a single conviction would be upped to life imprisonment. There is no parole in the federal justice system.
- Those convicted of providing "advice or assistance" to cyber crooks, or harboring or concealing a computer intruder, would face the same legal repercussions as an intruder. Computer intrusion would also become a predicate offense for the RICO statutes.
- DNA samples would be collected from hackers upon conviction, and retroactively from those currently in custody or under federal supervision. The samples would go into the federal database that currently catalogs murderers and kidnappers.
Civil liberties groups have criticized the ATA for its dramatic expansion of surveillance authority, and other law enforcement powers.
But Attorney General John Ashcroft urged swift adoption of the measure.
Testifying before the House Judiciary Committee, Ashcroft defended the proposal's definition of terrorism. "I don't believe that our definition of terrorism is so broad," said Ashcroft. "It is broad enough to include things like assaults on computers, and assaults designed to change the purpose of government."

The Anonymous group became known for a series of well- publicized hacks and on government, and corporate websites.
Anonymous originated in 2003 on the imageboard 4chan. It was also associated with Wiki Encyclopedia Dramatica. Anonymous members (known as "Anons") can be distinguished in public by the wearing Guy Fawkes masks, based on the film “V for Vendetta”.
In its early form, the concept was adopted by a decentralized online community acting anonymously in a coordinated manner, usually toward a loosely self-agreed goal, and primarily focused on entertainment, or "Lulz". The Anonymous collective became increasingly associated with collaborative, international hacktivism. Anons undertook protests and other actions in retaliation against anti-digital piracy campaigns by motion picture and recording industry trade associations. Anons have publicly supported WikiLeaks and the Occupy movement. Related groups LulzSec and Operation AntiSec carried out cyberattacks on US government agencies, media, video game companies, military contractors, military personnel, and police officers.
Dozens of people have been arrested for involvement in Anonymous cyber-attacks, in countries including the US, UK, Australia, the Netherlands, Spain, and Turkey. Evaluations of the group's actions and effectiveness vary widely. Supporters have called the group "freedom fighters" them as "a cyber lynch-mob" Times magazine called Anonymous one of the “100 most influential people in the world”.

LulzSec and Anonymous have taken credit for carrying out attacks against the CIA, Britain's Serious Organized Crime Agency, Sony Corporation, Mexican government websites and the national police in Ireland. Other victims included Rupert Murdoch's UK newspaper News International, Fox Broadcasting and Sony Pictures Entertainment.
No doubt some of these hacker groups will be reading this story, and I am completely open to anything that will promote their just cause. Even though I do not condone “real” terrorist acts, I think it’s fair to tell the Hackers’ side of the story - their beliefs, passions and motivations.
Until people realize, and understand, the motivation behind such acts, people will always condemn their actions. Negative press reports from newspapers with overt political agendas have added fuel to the fire.
I am not fully condoning the hacker’s behavior. Everyone has a right to their own opinions, preferences, cultures and ideologies.
Like many groups out there, there are some bad apples... but there are also some great thinkers who can inspire us all to make this world a better place for all nations.
 Dexter Phoenix has worked as a staff and freelance photographer since the mid-1990's and has a wealth of professional experiences on his resume. We welcome his presence to our staff and Salem-News.com.
Dexter Phoenix has worked as a staff and freelance photographer since the mid-1990's and has a wealth of professional experiences on his resume. We welcome his presence to our staff and Salem-News.com.
This native of Great Britian moved to Los Angeles in 2007, where he photographed general news, general Interests, sports, freelance model photo work, and also stock images. Dexter Phoenix has had photos published world wide, in many magazines and newspapers and online. Throughout the course of his career he has experience with technology of all imaginable types. As a photographer Dexter has covered stories in Norway, Sweden, Italy, Spain, Great Britain, France, Mexico, Israel, Palestine, Lebanon, Turkey, Somalia, Tunisia, Algeria. Angola, Iran, Dubai, Saudi Arabia, Brazil, Colombia, and the United States. Email inquiries about photo purchase to: innocent_p0stcard@hotmail.com
 |
 |
 |
Articles for February 19, 2014 | Articles for February 20, 2014 | Articles for February 21, 2014


googlec507860f6901db00.html
Quick Links
DINING
Willamette UniversityGoudy Commons Cafe
Dine on the Queen
Willamette Queen Sternwheeler
MUST SEE SALEM
Oregon Capitol ToursCapitol History Gateway
Willamette River Ride
Willamette Queen Sternwheeler
Historic Home Tours:
Deepwood Museum
The Bush House
Gaiety Hollow Garden
AUCTIONS - APPRAISALS
Auction Masters & AppraisalsCONSTRUCTION SERVICES
Roofing and ContractingSheridan, Ore.
ONLINE SHOPPING
Special Occasion DressesAdvertise with Salem-News
Contact:AdSales@Salem-News.com


Terms of Service | Privacy Policy
All comments and messages are approved by people and self promotional links or unacceptable comments are denied.
Dexter February 28, 2014 12:20 pm (Pacific time)
"Anonymous" it's always good to hear from all walks of life . I super appreciate your comment on here . Everyone needs to learn from this , and I agree completely on what you have said . All I can say is ... Be safe out there , and do what you believe in . Again thank you for leaving such a comment .
Anonymous February 26, 2014 9:15 am (Pacific time)
Dexter it appears England, and most of the world, is lagging behind the info curve. This is old news for us Americans, but then we have always been ahead, and that's why we were able to save England and all of Europe from the Nazi's and communists, because of peerless talent in having the best of the best as American citizens, always willing to help those who are incapable of handling their own affairs. Though communism is once again gaining ground very quickly in England. Sorry about that, but you are on your own now for we have some horrible leadership that has caused us extreme injury. When we resolve that, hopefully we can once again save you from yourselves.
Dexter February 24, 2014 4:02 am (Pacific time)
Thank you Mac
Mac February 23, 2014 1:15 am (Pacific time)
Thanks for the article and we can say - based on our knowledge & experiences - that the story is so true. By the way, I love the Apple logo with the NSA symbolic… I’m an owner of a respectable security app company and we, our customers and also our competitors have the sneaking suspicion, that Apple removing security apps, because Apple needs to have/use and/or all these apps make iOS look weak, insecure and not optimal, and because of that Apple has been removed many well known security apps without an explanation… but that’s another story. Keep up the good work Dexter.
Dexter February 22, 2014 6:39 pm (Pacific time)
My email has been blocked! Nice .
Splint February 22, 2014 6:26 pm (Pacific time)
the rest .............
Dexter February 22, 2014 6:08 pm (Pacific time)
Thank you Anonymous.Be safe out there
Dexter February 22, 2014 1:01 pm (Pacific time)
Thank you "Anonymous" . Be safe out there .
Anonymous February 22, 2014 12:12 pm (Pacific time)
You tell it like it is Mr. Phoenix.
Reprisal February 22, 2014 12:02 pm (Pacific time)
Someone give this guy a medal . Ballsy story, respect.
[Return to Top]©2026 Salem-News.com. All opinions expressed in this article are those of the author and do not necessarily reflect those of Salem-News.com.